Data Security in Zoho CRM – Overview
Introduction
In today’s digital landscape, data security is more critical than ever – especially for businesses involved in e-commerce or working across multiple teams and networks. Zoho CRM offers a robust suite of security features designed to control who can view, access, and manage your organization’s data.
This guide walks you through Zoho CRM’s security options – ranging from user roles to record sharing – and shows you how to protect sensitive data while ensuring efficient collaboration.
Step-by-Step Instructions:
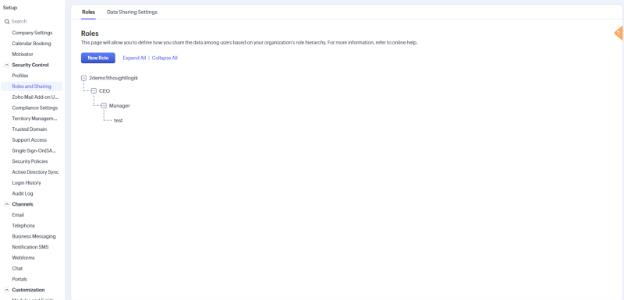
1. Role-Based Security
Control data visibility based on your organization’s hierarchy.
Role-based security allows users to access records owned by their subordinates. It’s especially useful for aligning data access with reporting lines.
- Go to Setup > Security Control > Roles
- Create a hierarchy of roles based on your org structure
- Assign users to the appropriate roles
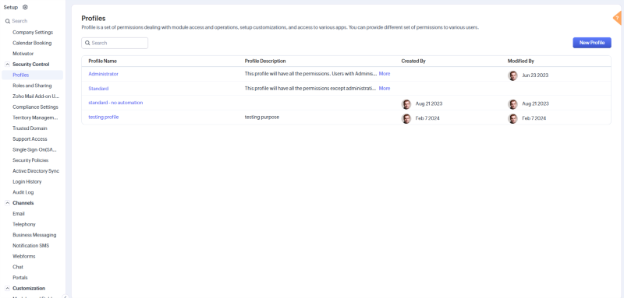
2. Profile-Based Security
Define what users can do inside Zoho CRM.
Profiles control access to features, tools, and modules. This helps you grant permission based on job function without impacting data access directly.
- Go to Setup > Security Control > Profiles
- Choose or create a profile (e.g., Sales Rep, Admin, Manager)
- Customize access to modules, views, and permissions
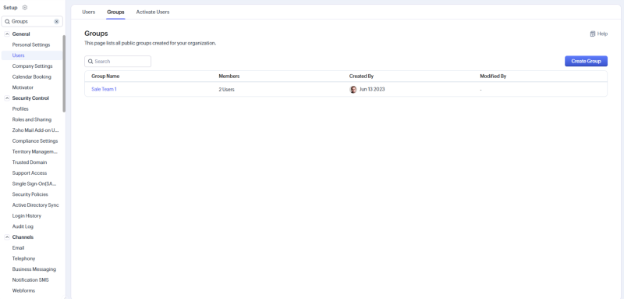
3. Group-Based Security
Allow cross-functional data access through user groups.
Groups let you share data among users with similar responsibilities, regardless of their position in the role hierarchy.
Use cases:
- Peer teams collaborating across regions
- Cross-department workflows
Steps to configure:
- Go to Setup > General > Groups
- Create a group and add relevant users
- Use the group for sharing rules or approvals
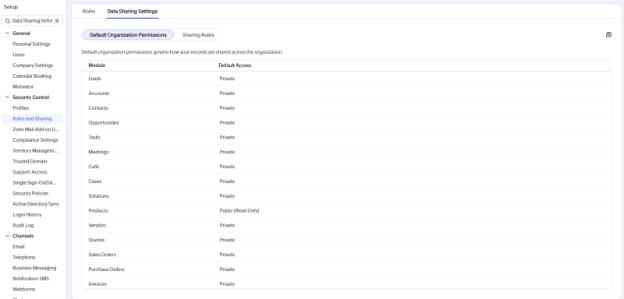
4. Data Sharing Rules
Expand access beyond the role hierarchy.
Sometimes, teams need access to data owned by others. Sharing rules allow for this by enabling access at the module level.
- Navigate to Setup > Security Control > Data Sharing Settings
- Define sharing rules between roles or groups
- Set permission levels (Read Only, Read/Write)
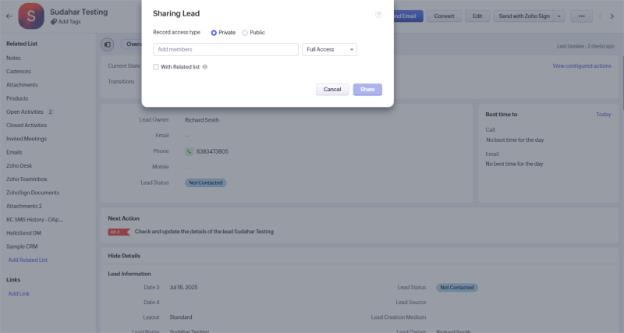
5. Record Sharing
Grant access to individual records for specific users or teams.
You can manually share a record with a peer or manager if they need temporary or one-time access.
- How to share a record:
- Open a record in any module
- Click the Share button
- Select the user or group and choose permission level
6. Data Encryption
Data is extremely sensitive and confidential. Zoho CRM helps you secure your data by encrypting it. Encryption is the process by which the raw data is encoded and can only be decoded by the authorized user. This blocks unauthorized parties from gaining access to your data in Zoho CRM
7. IP Restriction
Prevent unauthorized access by restricting CRM logins to specific IP addresses. This is especially useful for remote teams or when accessing CRM from controlled environments.
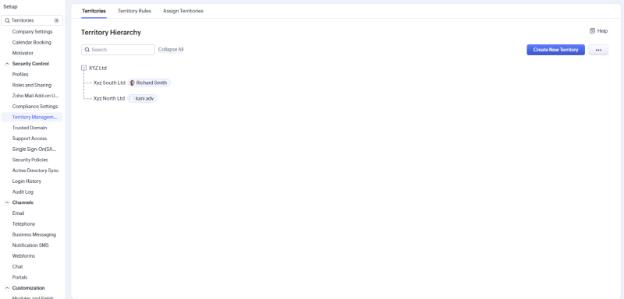
8. Territory Management
Organize your CRM data geographically or by business rules.
Territory management helps you assign accounts based on industry, region, or other custom logic – rather than ownership.
- Go to Setup >Security Control > Territory Management
- Define territories based on zip codes, industries, revenue brackets
- Assign users and access permissions to each territory
9. Zoho Mail Add-on Access
Manage access to CRM-integrated email features using Zoho Mail Add-on settings. Control who can send, receive, and manage email conversations directly from CRM.